Nmap is a security auditing tool used in the field of cybersecurity for actively enumerating a target system/network. It is one of the most widely used tools by network administrators and, conversely, by malicious actors for reconnaissance (enumeration), which is the first step in the 5 stages of hacking. Nmap is used to actively probe a target network for the presence of active hosts (host discovery), scan ports, detect the operating system, and gather information about the version and active services running on the hosts. Nmap achieves this by employing packet sending and response analysis techniques. To learn more, please refer to the Nmap article.
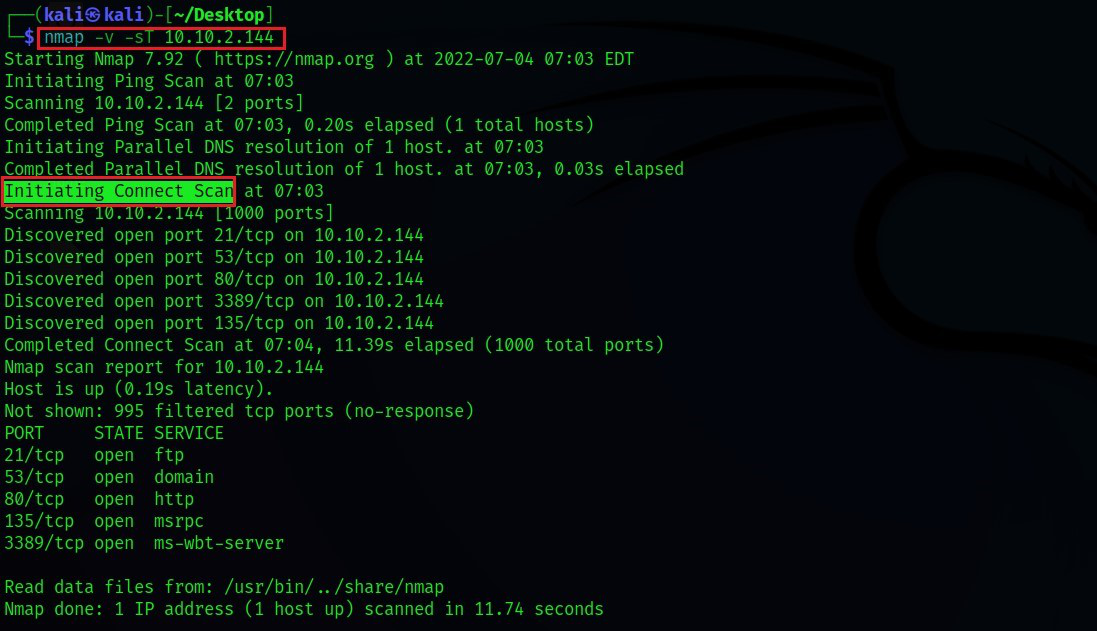
Port scanning is one of the features of Nmap in which the tool determines the state of ports on active hosts in the network. The port status can be open, filtered, or closed. To run Nmap, simply enter nmap in the command line and add the necessary switches according to the scanning type to initiate a specific scanning method.
Example: nmap -sS 192.168.0.1-192.168.0.52
This command runs Nmap with TCP SYN scanning (-sS) and scans the specified range of IP addresses for active hosts and services.
Types of port states:
Open:An open status means that the port is open, and an active service is running on it.Filtered:A filtered status means that the corresponding port may be hidden behind a firewall, and its status remains unknown.Closed:A closed state means that the port is closed on the host.
Various port scanning methods in Nmap
1.TCP Connect Scanning: TCP Connect scanning uses the concept of full three-way handshaking to determine whether a given port is open, filtered, or closed based on the response received. Nmap sends a TCP request packet to each specified port and determines the port’s status based on the response received. According to RFC 793,
If the connection does not exist (CLOSED), a reset is sent in response to any incoming segment except another reset. In particular, SYNs addressed to a non-existent connection are rejected by this means.
- In essence, this means that if
Nmapsends aTCP requestto a closed port with theSYN flagset, it receives aTCP packetwith theRESET flagset from the target server. This informsNmapthat the specified port is"closed." - On the other hand, if the port is genuinely
"open,"Nmapreceives a response with theSYN/ACK flagsset in response to the packet sent byNmapwith theSYN flagset. - The third possibility is that if the port is filtered, most server firewalls are configured to simply drop incoming packets.
Nmapreceives no response in this case. Essentially, this means that the port is operating behind a firewall (i.e.,"filtered").
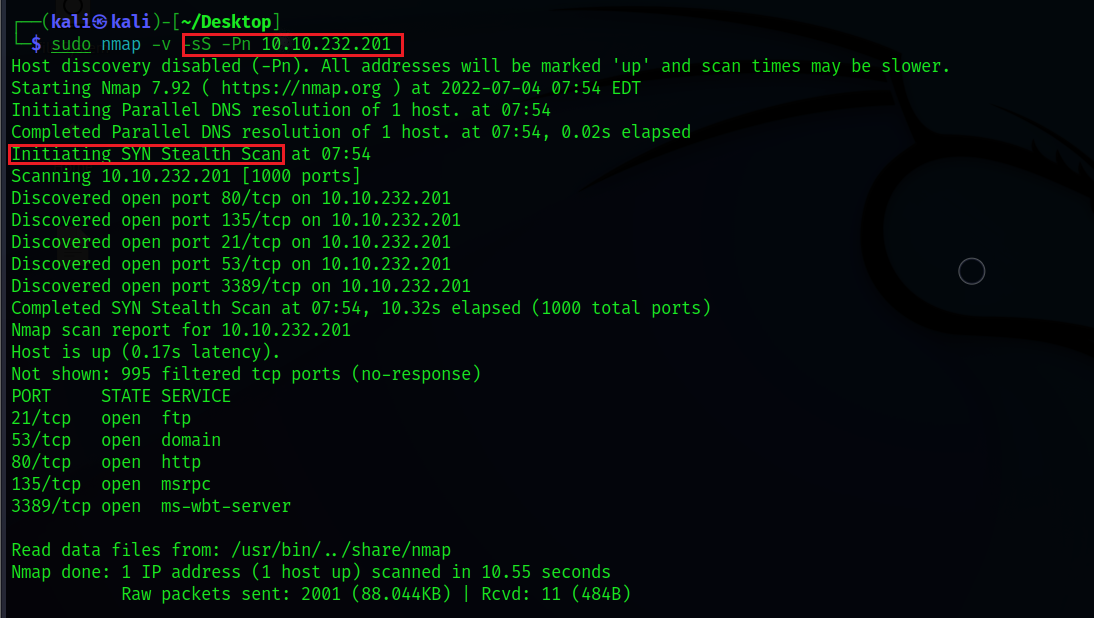
2. TCP SYN scanning (-sS) is often referred to as "half-open" or "stealth" scanning. SYN scanning works similarly to TCP Connect scanning with closed and filtered ports, meaning it receives the FIRST packet for a closed port and doesn’t respond for filtered ports. The only difference is how they handle open ports. SYN scanning sends a response packet to the server with the RESET flag set (but not ACK, which is typically used by default in a full three-way handshake) after receiving a SYN/ACK from the target server. This is done to prevent the server from constantly sending connection establishment requests and thus reduce scanning time.
This type of scanning is called stealth scanning due to the following advantages:
- Faster, as it doesn’t require a full three-way handshake to be completed.
- Some applications often only log those connections that are fully established. Therefore, applications listening on open ports do not log these connections, making
SYN scanning"stealthy."
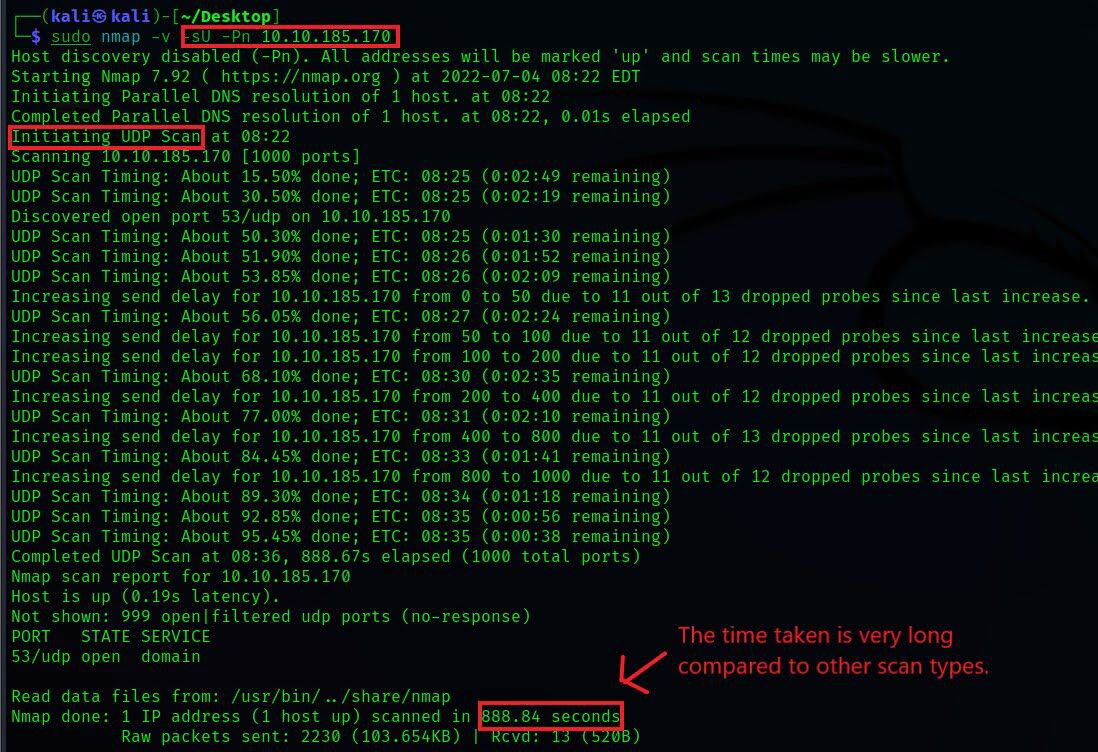
3. UDP scanning (-sU) in contrast to TCP does not perform handshaking to establish a connection before sending data packets to the target port. Instead, it sends packets in the hope that they will be received by the target port. This is why UDP connections are often referred to as "stateless.". This type of connection is more efficient when speed outweighs quality, such as in video streaming. Since there will be no acknowledgment from the target port that it received the packet, UDP scanning becomes more complex and much slower.
- When there’s no response from the target port after sending a
UDP packet, it often means that the port is either"open"or behind a firewall, i.e.,"filtered,"and in this case, the server simply drops the packet without responding. UDP scanningcan effectively identify closed ports because thetarget UDP portresponds with anICMP packetindicating that the port is unreachable.
The scanning methods listed below are less likely to be used in real-time, but it’s worth understanding the principles behind them. They are said to be even more stealthy than "SYN stealth" scanning.
For the types of scanning listed below, when a packet is sent to a "closed" port, there will be no response from the target port, which is very similar to UDP scanning. When these scanning types do not receive a response, they mark the port as open/filtered. According to RFC 793, for disguised packets, closed ports on the server are required to respond with the FIRST TCP packet and not respond at all for open ports.
TCP NULL Scan (-sN):NULLscanning, as the name suggests, sends aTCP packetwithno flagsset. If the port is closed, the host responds withRST.TCP FIN Scan (-sF):FINscanning, instead of sending completely empty packets, sends a packet with theFIN flagset. If the port is closed, the host responds withRST.TCP XMAS Scan (-sX):XMASscanning sends a packet with theURG, PSH, and FIN flagsset. This scanning got its name because it looks like a Christmas tree when viewed as a packet capture inWireshark. If the port is closed, the host responds withRST.