Subdomain takeovers pose a significant security risk to organizations, potentially allowing malicious actors to gain unauthorized control over abandoned or misconfigured subdomains. Understanding the concept of subdomain takeovers involves exploring the normal operations of subdomains, the concept of dangling DNS, and the potential consequences of a successful takeover. By familiarizing ourselves with these aspects, we can better comprehend the importance of implementing robust preventive measures.
Normal Operations of Subdomains
In a typical DNS setup, subdomains are used to organize and categorize specific services or functionalities within a larger domain. For instance, a company might have subdomains for services like mail.example.com, store.example.com, or blog.example.com. These subdomains are intended to be controlled and managed by the organization, with DNS records accurately pointing to active resources.
Dangling DNS
Dangling DNS occurs when a subdomain’s DNS record continues to exist even though the associated service or resource has been decommissioned or moved elsewhere. This can happen due to oversight, poor management practices, or when a third-party service provider is no longer in use. Dangling DNS leaves subdomains in a vulnerable state, as they can be potentially taken over by anyone who registers the expired or unclaimed domain.
Subdomain Takeovers and Consequences
A successful subdomain takeover provides an attacker with control over the compromised subdomain, allowing them to manipulate DNS responses and direct traffic to malicious destinations. This can lead to a range of harmful activities, including:
-
- Phishing Attacks: Attackers can craft convincing phishing campaigns by sending fraudulent emails from a legitimate subdomain, increasing the chances of successful deception.
-
- Malware Distribution: Compromised subdomains can be used to host and distribute malware, infecting unsuspecting users who visit the compromised subdomain.
- Reputation Damage: If a subdomain takeover leads to the dissemination of malicious or inappropriate content, it can tarnish the organization’s reputation and erode customer trust.
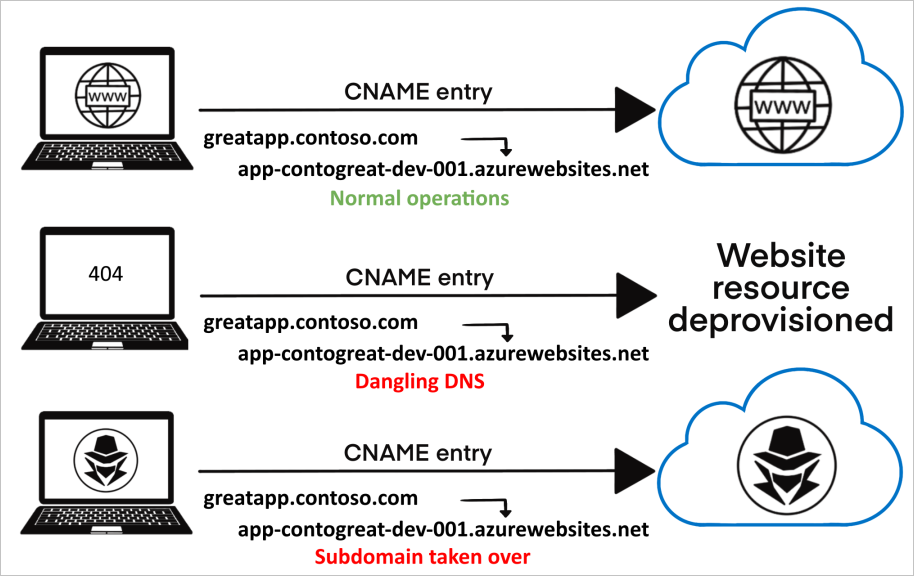
A common scenario for a subdomain takeover
- CREATION
a. You provision an Azure resource with a fully qualified domain name (FQDN) of app-contogreat-dev-001.azurewebsites.net.
b. You assign a CNAME record in your DNS zone with the subdomain greatapp.contoso.com that routes traffic to your Azure resource. - DEPROVISIONING
a. The Azure resource is deprovisioned or deleted after it is no longer needed.
At this point, the CNAME record greatapp.contoso.com should be removed from your DNS zone. If the CNAME record isn’t removed, it’s advertised as an active domain but doesn’t route traffic to an active Azure resource. This is the definition of a “dangling” DNS record.
b. The dangling subdomain, greatapp.contoso.com, is now vulnerable and can be taken over by being assigned to another Azure subscription’s resource. - TAKEOVER
a. Using commonly available methods and tools, a threat actor discovers the dangling subdomain.
b. The threat actor provisions an Azure resource with the same FQDN of the resource you previously controlled. In this example, app-contogreat-dev-001.azurewebsites.net.
c. Traffic being sent to the subdomain greatapp.contoso.com is now routed to the malicious actor’s resource where they control the content.
Prevention Measures
To mitigate the risk of subdomain takeovers, organizations should adopt the following preventive measures:
-
- Subdomain Inventory: Maintain an up-to-date inventory of all subdomains, ensuring that each one is actively managed and monitored.
-
- Regular Audits: Conduct regular audits to identify abandoned or misconfigured subdomains, promptly decommissioning them or updating DNS records as necessary.
-
- Third-Party Service Monitoring: Monitor the status of third-party services integrated into subdomains, ensuring they are actively maintained and properly configured.
-
- DNS Monitoring: Regularly review and monitor DNS configurations, promptly addressing any inconsistencies or outdated records.
-
- Access Control and Authentication: Implement strong access controls, multi-factor authentication, and privileged access management to prevent unauthorized access to domain and DNS management systems.
-
- Stay Informed: Stay up to date with the latest subdomain takeover techniques, security advisories, and best practices to adapt and strengthen preventive measures.
By proactively implementing these preventive measures, organizations can reduce the risk of subdomain takeovers, safeguard their online presence, and protect their customers from potential harm.