Please note that this article is purely educational. The author takes no
responsibility for any consequences resulting from reading it.
Introduction
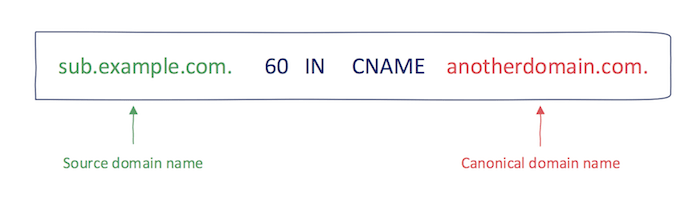
Subdomain takeover refers to the process of registering a non-existent domain name to gain control over another domain. The most common scenario involves the following steps:
- A domain name (e.g., sub.example.com) uses a CNAME record pointing to another domain (e.g., sub.example.com CNAME anotherdomain.com).
- At some point, the registration for anotherdomain.com expires, making it available for anyone to register.
- Since the CNAME record is not removed from the DNS zone of example.com, anyone who registers anotherdomain.com gains full control over sub.example.com until a new DNS record appears.
The consequences of subdomain takeover can be significant. By exploiting subdomain takeover, malicious actors can send phishing emails from a legitimate domain, execute cross-site scripting (XSS) attacks, or damage the reputation of a brand associated with the domain.
Subdomain takeover is not limited to CNAME records. It also affects NS, MX, and even A records (which are not covered in this publication). This post primarily focuses on CNAME records.
Now that you have a general understanding of the vulnerability associated with subdomain takeover and its impact, let’s move on to how to discover such subdomains.
Manual Method for Subdomain Discovery
First and foremost, we need to find all “dead” subdomains and their CNAME records. For this, we can use a simple command called dig. You can use it as follows:
The output of this command is crucial, and we will use it later. We need to see if any of these subdomains are “dead” and if they return any error messages or other responses.
If a domain returns an error message, we take the domain (in this case, herokuapp.com) from the dig command output and check if it can be taken over. Tools like can-i-take-over-xyz can be used for this purpose. Additionally, the availability of basic domain names can be checked using domain registrars such as Namecheap.
Automated Method for Subdomain Discovery
The method and process are the same, but tools can do all the work for us. I’m using a tool called subjack, written in Golang, which works very quickly.
Example Vulnerability Demonstration
Let’s walk through the steps of reproducing this vulnerability on the starbucks.com website. The full report can be viewed at the provided link.
Steps to reproduce:
- Using dig, the author determined that the subdomain «d02-1-ag.productioncontroller.starbucks.com» was vulnerable to takeover. The record showed a status of NXDOMAIN and pointed to the CNAME: 3edbac0a-5c43-428a-b451-a5eb268f888b.cloudapp.net.
- Using this information, the author was able to create a new Azure cloud service named «3edbac0a-5c43-428a-b451-a5eb268f888b,» which would lead to the aforementioned CNAME record.
- Next, the author created a website and uploaded it to the cloud service using a guide from Microsoft.
- Finally, the author was able to view the uploaded site at http://d02-1-ag.productioncontroller.starbucks.com.
For reporting this vulnerability, the author received a reward of $2000.







Excellent resource!