The OSI model is a theoretical framework that helps in understanding and explaining the complexities of network communication. It breaks down the process into seven distinct layers, each responsible for specific functions. These layers work together to ensure data is transmitted reliably and securely across a network. By breaking down network operations into manageable components, the OSI model provides a standardized approach to designing and troubleshooting network systems.
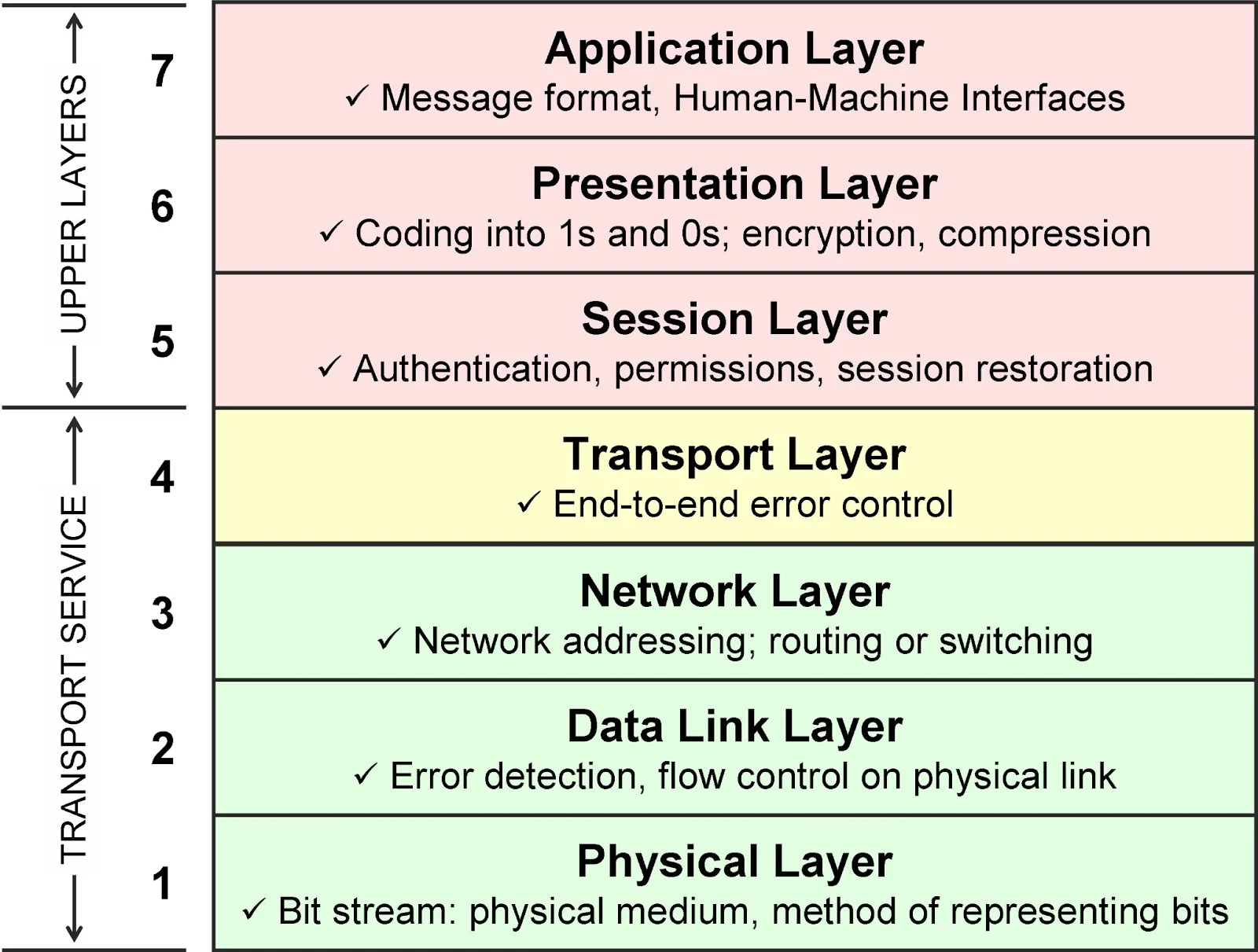
OSI Layers
Physical Layer (Layer 1):- The Physical Layer is the lowest layer of the OSI model and
deals with the physical medium over which data is transmitted. - It defines the electrical, mechanical, and functional specifications for the hardware, such as cables and switches.
Protocols:Ethernet, Token Ring, Wi-FiExamplesinclude Ethernet cables, fiber-optic cables, and wireless radio waves. The email message is converted into electrical signals, transmitted over a network cable, or sent wirelessly via radio waves.
- The Physical Layer is the lowest layer of the OSI model and
Data Link Layer (Layer 2):- The Data Link Layer is
responsible for creating a reliable link between two directly connected nodes. - It manages data framing, error detection, and flow control.
Protocols:HDLC, PPP, Ethernet MACExamplesinclude Ethernet switches and network interface cards (NICs). The email message is divided into smaller frames for transmission, and each frame is labeled with source and destination MAC addresses.
- The Data Link Layer is
Network Layer (Layer 3):- The Network Layer
handles the routing and forwarding of data packets. - It ensures data reaches its destination by using logical addressing (IP addresses) and making routing decisions.
Protocols:IP, ICMP, RIP, OSPFExamplesinclude routers and Layer 3 switches. The email message is routed through various network devices, including routers, which determine the best path to reach the recipient’s email server based on IP addresses.
- The Network Layer
Transport Layer (Layer 4):- The Transport Layer is
responsible for end-to-end communication between devices. - It manages data segmentation, error detection, and flow control.
Protocols:TCP, UDPExample:The email message is divided into segments and sent using a transport protocol like SMTP (Simple Mail Transfer Protocol) or POP3 (Post Office Protocol) to ensure reliable end-to-end communication.
- The Transport Layer is
Session Layer (Layer 5):- The Session Layer
establishes, maintains, and terminates communication sessions between two devices. - It manages session synchronization and data exchange.
Protocols:NetBIOS, RPC (Remote Procedure Call), and PPTP (Point-to-Point Tunneling Protocol).Example:The session layer manages the establishment and termination of the email session between the sender and the recipient.
- The Session Layer
Presentation Layer (Layer 6):- The Presentation Layer is responsible for
data translation, encryption, and compression. - It ensures that data is presented in a format that the application can understand.
Protocols:JPEG, GIF, TIFF, MPEG The email content may be encrypted to ensure privacy and compressed to reduce transmission time.
- The Presentation Layer is responsible for
Application Layer (Layer 7):- The Application Layer is
the top layer and interacts directly with end-user applications. - It provides services such as email, file transfer, and web browsing.
Protocols:FTP, HTTP, SMTP, DNSExamplesinclude HTTP for web browsing, SMTP for email, and FTP for file transfer. The email application (e.g., Outlook, Gmail) displays the email message to the user.
- The Application Layer is
Conclusion
The OSI model serves as a fundamental framework for understanding network communication, providing a clear and structured approach to comprehending the complex interplay of protocols and layers that enable data transfer across networks. By grasping the intricacies of the OSI model, cybersecurity professionals can better identify network vulnerabilities, troubleshoot network issues