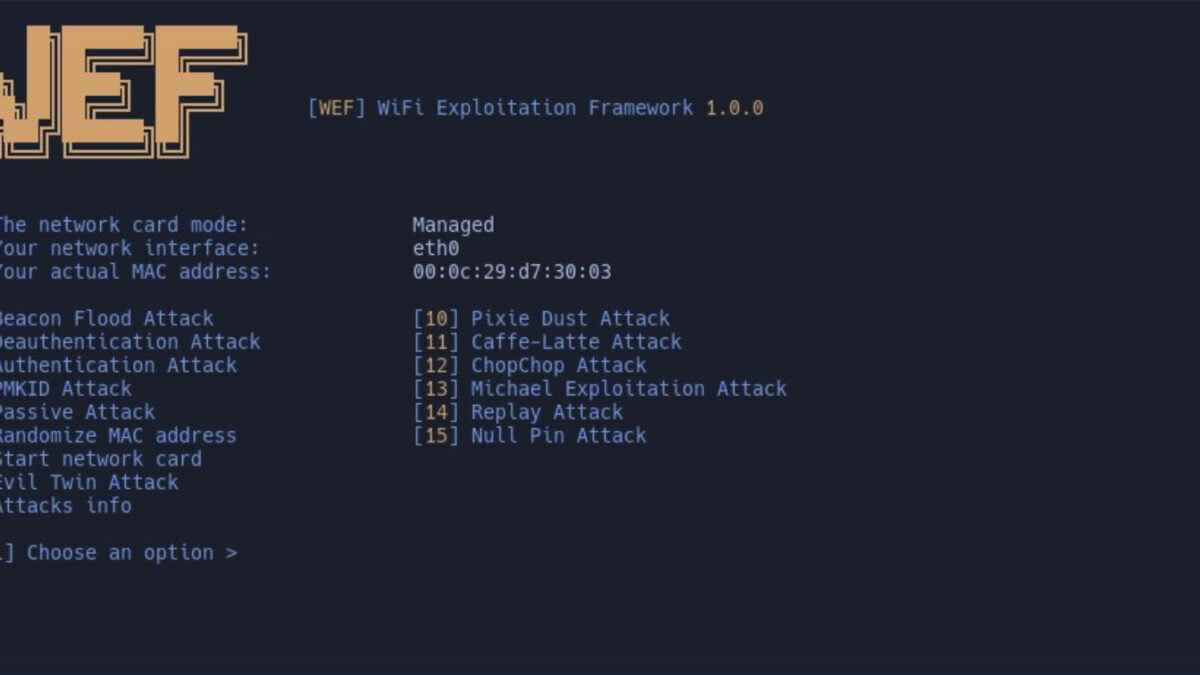
WEF is an advanced and versatile platform that encompasses a wide range of attack techniques for testing the security of Wi-Fi networks. With support for various attack types targeting WPA/WPA2, WEP, Bluetooth, and more, WEF provides security professionals with a comprehensive toolkit for identifying weaknesses and ensuring robust protection measures.
Supported Attacks
1. Deauthentication Attack
A deauthentication attack involves forcefully disconnecting devices from a Wi-Fi network by sending forged deauthentication packets. This attack disrupts the connection between devices and the network, effectively denying service to legitimate users and potentially allowing an attacker to intercept sensitive information.
Authentication-Based Attack: An authentication-based attack targets the authentication process of a Wi-Fi network. Attackers attempt to exploit vulnerabilities in the authentication mechanism to gain unauthorized access to the network. By circumventing or bypassing authentication protocols, attackers can infiltrate the network and compromise its security.
2. Beacon Attack
A beacon attack involves the manipulation of Wi-Fi beacon frames, which are broadcasted by access points to advertise the presence of a network. Attackers can use this attack to deceive devices by broadcasting fake beacon frames, enticing them to connect to malicious networks that appear legitimate. This attack aims to trick users into connecting to malicious access points.
3. PMKID Attack
A PMKID attack targets the Pre-Shared Key (PSK) authentication method used in WPA/WPA2-PSK networks. Attackers exploit weaknesses in the PMKID caching feature to retrieve hashed authentication credentials. By cracking these credentials offline, attackers can gain unauthorized access to the network.
4. EvilTwin Attack
An EvilTwin attack involves creating a malicious Wi-Fi network that mimics a legitimate network. Attackers set up an access point with the same SSID and security settings as the target network to deceive users into connecting to the malicious network. This attack enables attackers to intercept sensitive information or perform other malicious activities.
5. Passive/Stealthy Attack
Passive/Stealthy refers to a type of attack or behavior that emphasizes remaining undetected or minimizing its impact on the target system or network. In the context of cybersecurity, passive or stealthy attacks are designed to avoid detection by security systems, firewalls, or intrusion detection mechanisms, making them harder to identify and mitigate.
6. Pixie Dust Attack
The Pixie Dust Attack is a method of exploiting vulnerabilities in the Wi-Fi Protected Setup (WPS) protocol, a feature designed to simplify the process of connecting devices to Wi-Fi networks. This attack takes advantage of weaknesses in the WPS implementation to bypass security measures and extract crucial network information, such as the Wi-Fi password.
7. Null PIN Attack
A Null PIN Attack, also known as a PINless attack or No-PIN attack, is a method used to exploit the vulnerabilities in the Wi-Fi Protected Setup (WPS) protocol. WPS is a feature designed to simplify the process of connecting devices to Wi-Fi networks by using a Personal Identification Number (PIN) as a form of authentication.
8. Chopchop Attack
A Chopchop attack is an encryption-based attack on WEP-encrypted Wi-Fi networks. Attackers exploit the vulnerabilities in the RC4 encryption algorithm used by WEP to decrypt packets without knowing the encryption key. This attack allows attackers to intercept and manipulate network traffic.
9. Replay Attack
A replay attack involves capturing and retransmitting data packets exchanged between devices in a Wi-Fi network. By replaying captured packets, attackers can deceive the network into accepting repeated or unauthorized actions, potentially compromising its security.
10. Michael Attack Exploit
The Michael attack exploit targets vulnerabilities in the TKIP (Temporal Key Integrity Protocol) encryption algorithm used in WPA networks. Attackers exploit weaknesses in TKIP to decrypt packets, retrieve encryption keys, and potentially gain unauthorized access to the network.
11. Cafe-Latte Attack
The Cafe-Latte Attack targets the weaknesses in the WEP encryption protocol, which was widely used in early Wi-Fi networks. By exploiting the flawed key scheduling algorithm and capturing enough encrypted packets, attackers can eventually crack the encryption key, gaining unauthorized access to network traffic.
12. Bluetooth Interference, Reading, and Writing Connections
Beyond Wi-Fi, WEF also supports attacks on Bluetooth technology. It allows for interference with Bluetooth signals, reading and analyzing Bluetooth connections, and even writing
Key Features and Capabilities
1. Diverse Attack Techniques
WEF offers a broad spectrum of attack techniques to simulate real-world scenarios. It includes deauthentication attacks, authentication-based attacks, beacon attacks, PMKID attacks, EvilTwin attacks, passive/hidden attacks, Elf dust attacks, zero PIN attacks, Chopchop attacks, replay attacks, Michael attack exploits, coffee-latte attacks, and more. This extensive arsenal empowers security experts to evaluate network vulnerabilities comprehensively.
2. WPA/WPA2, WPS, and WEP Attacks
The framework covers attacks targeting commonly used security protocols, such as WPA/WPA2, WPS, and WEP. By subjecting these protocols to rigorous testing, organizations can uncover potential weaknesses and address them before malicious actors exploit them.
3. Bluetooth Interference and Exploitation
WEF goes beyond Wi-Fi networks by supporting interference, reading, and writing connections in Bluetooth. This capability allows security professionals to assess and mitigate potential risks associated with Bluetooth devices and their interactions with wireless networks.
4. Monitor Mode and Frequency Support
The platform facilitates the monitoring of Wi-Fi networks by providing options to check monitor mode availability and status. Additionally, WEF supports attacks on both 2 GHz and 5 GHz frequencies, ensuring comprehensive coverage across different frequency bands.
5. Customizable Word List Selector
To enhance attack effectiveness, WEF offers a user-customizable word list selector. This feature enables security experts to tailor attacks specifically to their targets and increase the likelihood of successful exploitation.
6. Automatic Detection and Requirements
WEF streamlines the setup process by automatically handling and installing necessary dependencies. The framework takes care of installing essential tools and packages, such as aircrack-ng, reaver, mdk4, macchanger, hashcat, xterm, hcxtools, pixiewps, python3, btlejack, crackle, php, hostapd, and dnsmasq.
7. Automatic Handshake Cracking
With WEF’s automatic handshake cracking capability, security professionals can streamline the process of cracking Wi-Fi network handshakes. Handshake cracking is a crucial step in gaining unauthorized access to a protected network. By automating this process, WEF simplifies and accelerates the identification of weak or compromised passwords, enhancing the overall efficiency of security assessments.
8. Log Generator
The log generator feature in WEF enables users to generate detailed logs of their activities and attack sessions. These logs provide valuable insights and records of the testing process, allowing security professionals to analyze results, track progress, and document findings. The log generator enhances the overall visibility and traceability of Wi-Fi network assessments.
9. Multiple EvilTwin Attack Templates
The EvilTwin attack is a common method used to deceive Wi-Fi clients by impersonating a legitimate network. WEF provides users with multiple EvilTwin attack templates, enabling them to create convincing replicas of target networks and lure unsuspecting devices. This feature facilitates the identification of vulnerabilities in devices that automatically connect to familiar networks, enhancing the overall understanding of potential security risks.
10. Check Monitor Mode and its Status
Monitoring Wi-Fi networks is crucial for capturing and analyzing network traffic during security assessments. WEF includes a feature to check the availability and status of monitor mode. This capability ensures that users can effectively monitor network activity, capture relevant data, and perform advanced analysis to identify potential security weaknesses.
11. Attacks on 2 GHz and 5 GHz Frequencies
As Wi-Fi networks operate on different frequency bands, WEF supports attacks on both the 2 GHz and 5 GHz frequencies. By covering multiple frequency ranges, WEF provides comprehensive testing capabilities, enabling security professionals to assess the network’s resilience against potential attacks across various frequency bands.
12. Bluetooth Support (Interference, Reading, Writing)
In addition to Wi-Fi network assessments, WEF extends its capabilities to Bluetooth technologies. The framework supports various Bluetooth-related functionalities, including interference, reading, and writing connections. This feature enables security professionals to assess the security of Bluetooth devices and their interactions with wireless networks, ensuring a comprehensive evaluation of potential vulnerabilities.
How to use WEF (Wi-Fi Exploitation Framework)?
General platform usage
wef -i wlan0 # Your interface name may varyorwef --interface wlan0
After launching the application, enter "help" to view additional features and useful information.
If you don’t want to scan access points for every attack, you can do something like this:
set name my-wifi # Specify the name for the attack
set time 60 # Determine the total duration of time-based attacks
set packets 15 # Define the number of packets to be sent by certain attacks
Requirements:
Do not install them manually; WEF will take care of it if you don’t have them already.aircrack-ng
reaver
mdk4
macchanger
hashcat
xterm
hcxtools
pixiewps
python3
btlejack
crackle
php
hostapd
dnsmasq
Additionally:
If you use bspwm, you can add this line to your bspwmrc to launch a floating Windows xterm for a more aesthetically pleasing design:
bspc rule -a XTerm state=floating