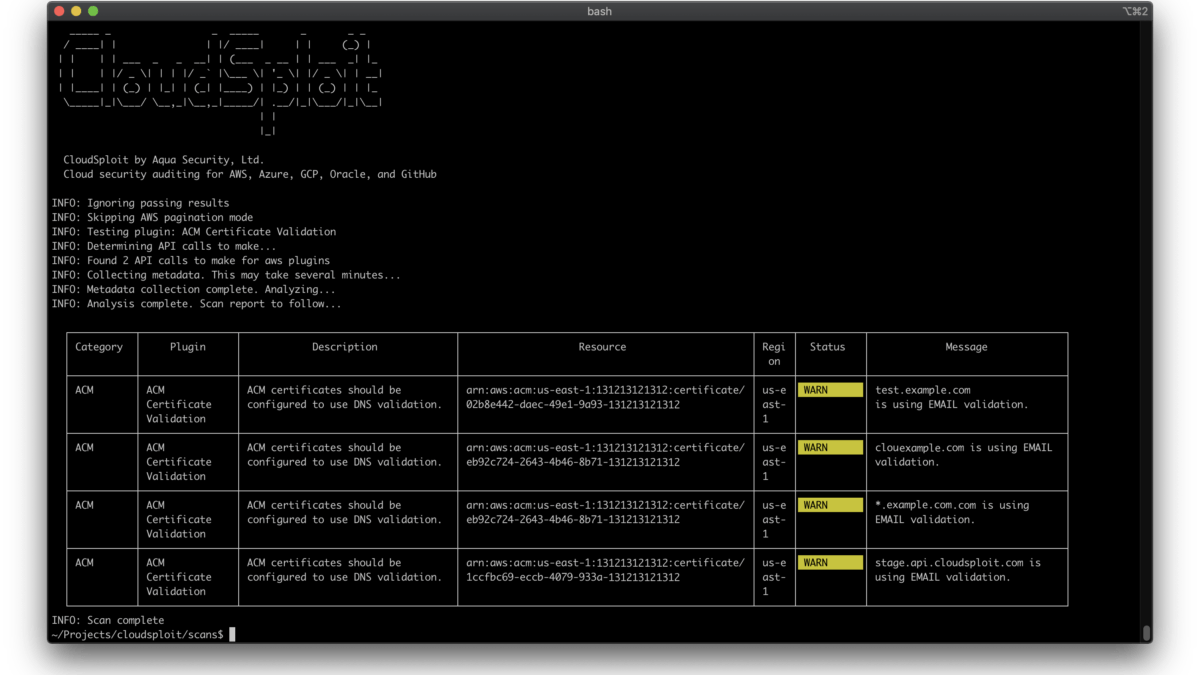
CloudSploit is an open-source tool that helps you to identify security risks in your cloud infrastructure. It can be used to scan AWS, Azure, GCP, and OCI accounts for misconfigurations and other security vulnerabilities. CloudSploit is easy to use and can be run from the command line or as a Docker container.
Here are some of the strengths of CloudSploit:
- It is easy to use. CloudSploit is a command-line tool, so it is easy to learn and use. You can run it from the command line or as a Docker container.
- It is comprehensive. CloudSploit can scan your cloud infrastructure for a wide range of security risks, including misconfigurations, open ports, and insecure permissions.
- It is up-to-date. CloudSploit is constantly being updated with new security checks. This means that you can be sure that you are always protected against the latest threats.
Here are some of the places where you can use CloudSploit:
- In your own cloud infrastructure. CloudSploit can be used to scan your own cloud infrastructure for security risks. This can help you to identify and fix security vulnerabilities before they are exploited by attackers.
- In a cloud security assessment. CloudSploit can be used as part of a cloud security assessment. This can help you to identify security risks in your cloud infrastructure and make recommendations for how to improve your security posture.
- In a cloud security training program. CloudSploit can be used as a training tool to help people learn about cloud security. This can help to raise awareness of cloud security risks and how to mitigate them.