More than 40,000 Cisco devices running the IOS XE operating system have fallen victim to an exploit following the discovery of a high-severity vulnerability known as CVE-2023-20198.
As of now, there is no patch or workaround available for this vulnerability, leaving customers with just one recommended action to secure their devices: “disable the HTTP Server feature on all internet-facing systems.”
The impacted networking equipment includes various devices, such as enterprise switches, industrial routers, access points, wireless controllers, aggregation hardware, and branch routers.
Thousands of Cisco Devices Exploited
Initially estimated at around 10,000 affected devices, the number has grown considerably as security researchers scoured the internet for a more accurate count.
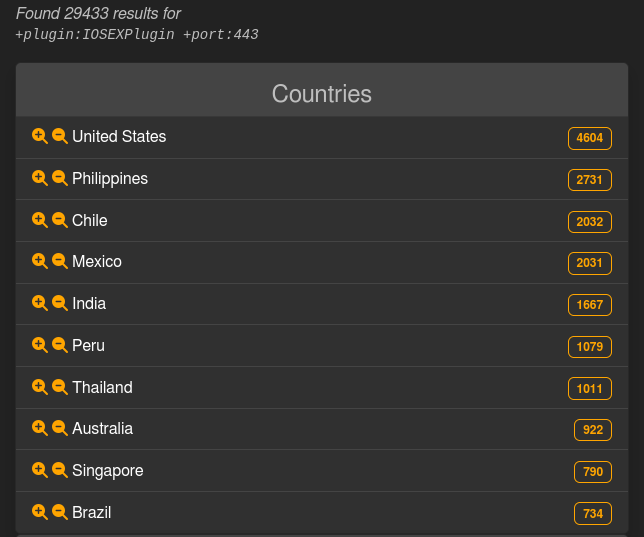
The LeakIX engine, which indexes public web services and applications, reported approximately 30,000 infected devices, not accounting for rebooted systems. They used Cisco’s provided indicators of compromise (IoCs) to identify successful exploitations in the United States, the Philippines, and Chile.
LeakIX results for Cisco IOS XE devices exposed online
Additionally, the private CERT from Orange revealed that over 34,500 Cisco IOS XE IP addresses were compromised due to CVE-2023-20198 exploitation. They also published a Python script for detecting the presence of the malicious implant on network devices running Cisco IOS XE.
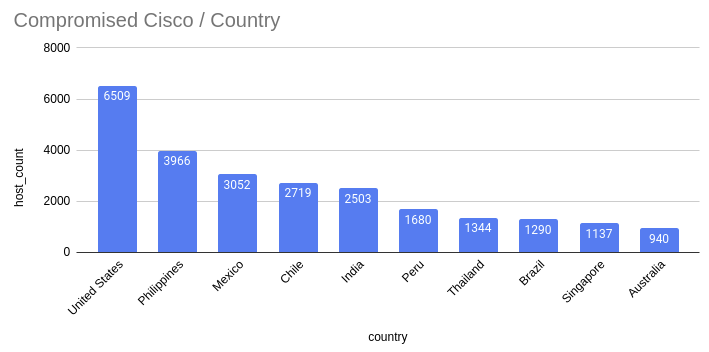
An update from the Censys search platform on October 18 indicated an increased count of compromised devices, reaching 41,983.
Censys results for Cisco IOS XE hosts on the public web
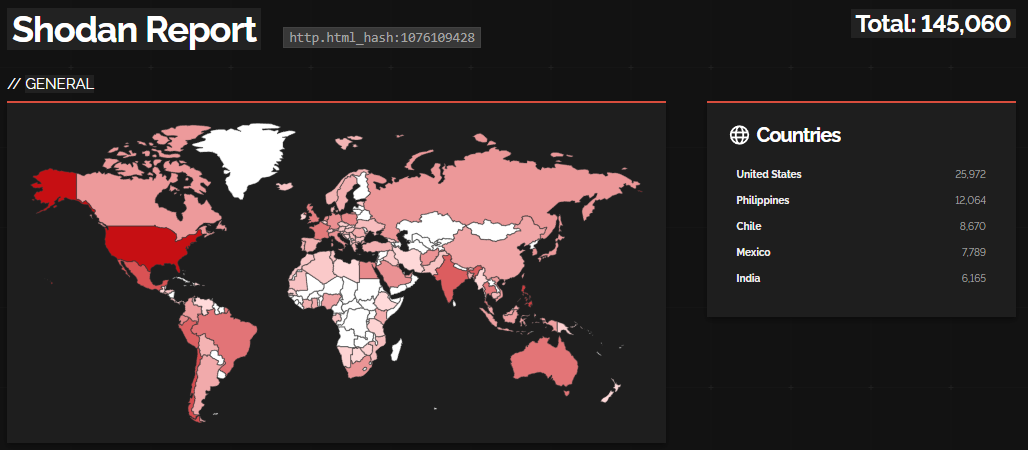
While an exact figure for publicly accessible Cisco IOS XE devices remains challenging to ascertain, Shodan data reveals over 145,000 hosts, primarily located in the U.S.
Security researcher Yutaka Sejiyama conducted a similar search on Shodan and identified nearly 90,000 exposed Cisco IOS XE devices susceptible to CVE-2023-20198. Notably, many of these devices are associated with communications providers like Comcast, Verizon, and others, as well as various institutions, including medical centers, universities, government entities, and more.
Shodan results for exposed Cisco IOS XE systems
source: BleepingComputer
This situation underscores the importance of not exposing the IOS XE login screen on the Internet, as recommended by Cisco, to prevent such vulnerabilities and breaches. Many organizations unknowingly expose these devices to the public web, potentially leaving them vulnerable to exploitation.
Risk Persists Even After Device Reboot
Although Cisco officially disclosed CVE-2023-20198 on Monday, malicious actors had already been exploiting it as a zero-day vulnerability before September 28th. This exploitation allowed them to create a high-privilege account on compromised devices, granting them complete control.
In response to the threat, Cisco has updated its advisory with fresh attacker IP addresses, usernames, and introduced new rules for the Snort open-source network intrusion detection system and intrusion prevention system.
Researchers have observed that the attackers employ a malicious implant in these assaults, which lacks persistence and is eradicated upon device reboot. However, the newly established accounts remain active, possessing level 15 privileges, granting them full administrative control over the compromised device.
Cisco’s analysis indicates that the threat actor engages in device profiling and conducts initial reconnaissance activities. The attacker is also observed clearing logs and eliminating users, presumably in an effort to conceal their actions.
While it is suspected that a single threat actor is responsible for these attacks, the initial delivery method could not be definitively determined.
Cisco, for now, has not disclosed further details about these attacks but has committed to providing more information once the investigation is completed and a fix becomes available.