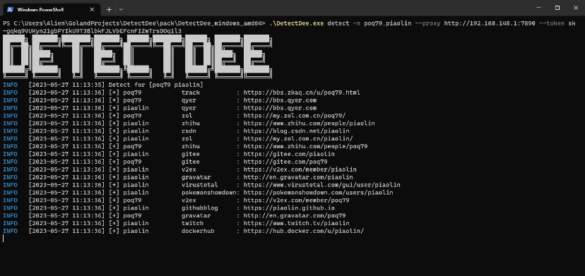
DetectDee | Hunt down Social Media
DetectDee is a tool that can help you find and delete forgotten social media accounts. It does this by using…
Privacy Badger | Powerful browser extensions
Privacy Badger is a free and open-source browser extension that blocks trackers. Trackers are small pieces of code that are…
Unredacter | Unredact Text Quickly and Easily
Unredacter – The tool for removing pixelation or the main argument against this method of hiding information. Here are some…
OpenVAS: Way to Robust Vulnerability Assessment
What is OpenVAS? OpenVAS, or Open Vulnerability Assessment System, is a powerful tool designed to detect vulnerabilities in software and…
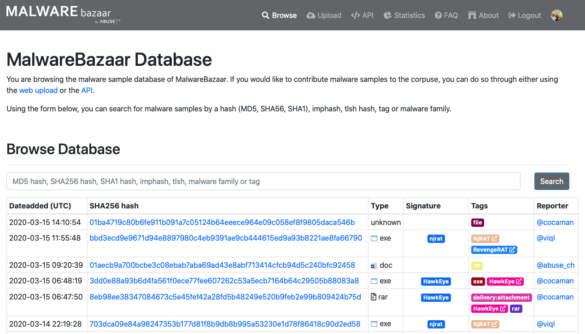
MalwareBazaar – Malware Sample Database
MalwareBazaar is a comprehensive platform that provides an extensive collection of malware samples, offering a unique opportunity for researchers, cybersecurity…
Secure Your Website with Security Headers (Windows/Linux)
With the rise of cybersecurity threats, protecting your website and its visitors is of utmost importance. One effective way to…
ProtonVPN Pros vs. Cons: Making an Informed Choice
Get ProtonVPN In today’s digital landscape, ensuring online privacy and security has become increasingly important. Virtual Private Networks (VPNs)…
Defending Against Zero-Click Attacks: The Silent Threat
Zero-click attacks have emerged as a formidable challenge for organizations, as they exploit vulnerabilities without any user interaction,…
Hacking a Company with 0-Click Email Attack
Phishing Attacks Phishing attacks have emerged as a prominent method employed by malicious actors. Among the various tactics used, a…
Defending Against Cafe-Latte: Strengthening Wi-Fi Security
Understanding the Cafe-Latte Attack The Cafe-Latte Attack targets the weaknesses in the WEP encryption protocol, which was widely used in…