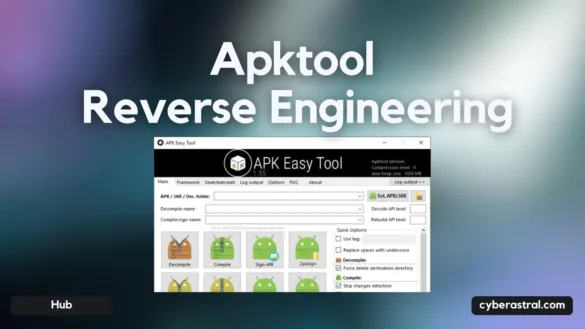
Apktool | Reverse Engineering Tool
It is a tool for reverse engineering 3rd party, closed, binary Android apps. It can decode resources to nearly original…
What is DNS Spoofing?
Today, the internet has become an integral part of our lives. From banking to shopping to travel, every aspect of…
Repository With Free Anonymous Proxies
proxy-list GitHub repository containing anonymous HTTP, SOCKS4, SOCKS5 proxies that are updated and checked approximately every 15 minutes. The repository…
Hackers Exploit Zero-Day Vulnerability to Compromise Cisco Devices
More than 40,000 Cisco devices running the IOS XE operating system have fallen victim to an exploit following the discovery…
5 Tools for Directory Traversal Attack
In the last article, we discussed How to Disable Directory Listing on a Web Server and why it can be…
How to Disable Directory Listing on your Web Server
What is Directory Listing? Directory listing, also known as folder listing or directory index, is a feature provided by web…
Mastering Vulnerability Analysis: Tools and Methods
Vulnerability analysis is a fundamental aspect of cybersecurity that involves identifying weaknesses and potential threats in systems and applications. In…
CSI Linux | Useful OS in the Cybersecurity World
Introduction You can no longer hide from Big Brother. Thousands of virtual “eyes” are watching you, creating a detailed digital…
OWASP Top 10: A1 SQL Injection
Vulnerability A1 Injection currently holds the 1st position in the OWASP Top 10 ranking, which means it is responsible for…
TCP: What Kind Of Protocol Is It?
In what cases do we need TCP packet analysis? In practice, modern network traffic analysis systems have an extensive database…