Deauthentication Attack: Understanding Wi-Fi Network Disruption
Understanding the Deauthentication Attack The deauthentication attack involves the deliberate disruption of the connection between a client device and a…
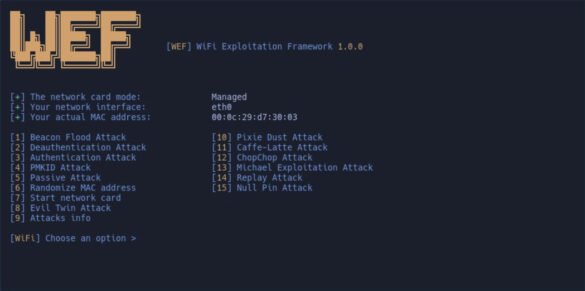
WEF | Time to get familiar with Wi-Fi Exploitation Framework
WEF is an advanced and versatile platform that encompasses a wide range of attack techniques for testing the security of…
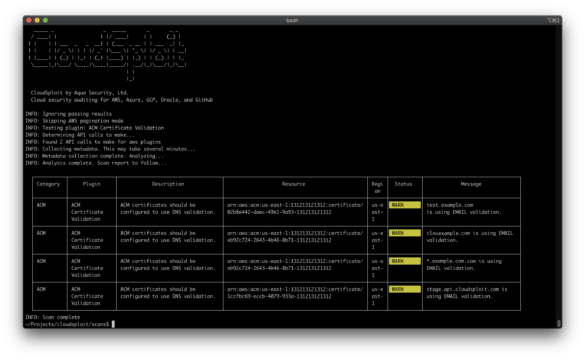
How to Protect Your Cloud Infrastructure with CloudSploit
CloudSploit is an open-source tool that helps you to identify security risks in your cloud infrastructure. It can be used…
Burp Suite: The Power of Web Application Security Testing
In today’s interconnected world, web application security is of paramount importance. Organizations need robust tools to identify vulnerabilities and protect…
Diving Deeper into the Intricacies of Burp Suite
Scanning phase involves analyzing traffic and application behavior to identify vulnerabilities and other issues. Burp Scanner uses a wide range…
Russian LockBit Operator Arrested, Law Enforcement Sends Message
A 20-year-old Russian national was arrested in Arizona on Thursday for his alleged involvement in the LockBit ransomware operation. Ruslan…
Shielding Your Apps: Top 5 Best Practices for Application Security
Welcome back, fearless app defenders! In our previous article, we uncovered the basics of application security and why it’s essential…
Spotlight on Application Security: Understanding the Basics
Hey there, tech-savvy readers! Welcome to a special edition where we shed light on the fascinating world of application security….
Safeguarding Your Data: An Overview of Data Security
In today’s digital age, data plays a pivotal role in our personal and professional lives. From financial records to sensitive…
Best Practices to Safeguard Your Databases Against Common Vulnerabilities
Databases serve as the backbone of modern applications, housing valuable and sensitive information. However, they are often targeted by attackers…