SSTI: Server-Side Template Injection Guide.
What is SSTI? Server-Side Template Injection is a vulnerability where an attacker injects malicious code into a template to execute…
TorGhost | Your Best Friend in Anonymous Traffic
TorGhost is an anonymization script designed to enhance online privacy by routing all internet traffic through the Tor network. This…
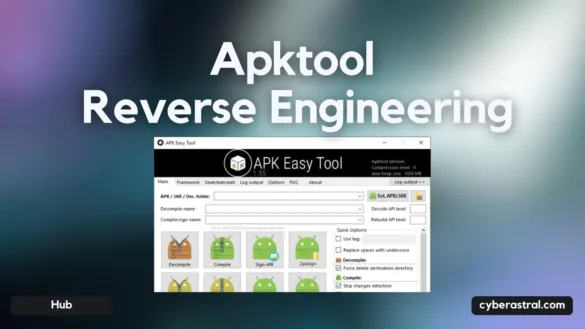
Apktool | Reverse Engineering Tool
It is a tool for reverse engineering 3rd party, closed, binary Android apps. It can decode resources to nearly original…
Repository With Free Anonymous Proxies
proxy-list GitHub repository containing anonymous HTTP, SOCKS4, SOCKS5 proxies that are updated and checked approximately every 15 minutes. The repository…
5 Tools for Directory Traversal Attack
In the last article, we discussed How to Disable Directory Listing on a Web Server and why it can be…
Burp Suite: Delving into Security Auditing
Introduction The scanning phase in Burp Suite is a critical step in the process of assessing the security of web…
Top 10 XSS Tools In 2023
To assist security professionals and ethical hackers in their mission to protect web applications, we have compiled a list of…
Sniffnet – Network Monitoring
What is Sniffnet? Sniffnet is a free and open-source application for Linux, macOS, and Windows. It is a network monitoring…
5 Best Scanners for Penetration Testing
1. Nmap Nmap is a free and open-source network scanner that can be used for a variety of purposes, including:…
Katana | Web Application Security Scanner
Katana is an open-source web application security scanner that automates the process of identifying vulnerabilities in web applications. It was created…