Silent Shadows: The Hidden Dangers of Passive/Stealthy Wi-Fi Attacks
In the realm of cybersecurity, an intriguing and elusive breed of attacks known as Passive/Stealthy attacks have emerged. These attacks…
Wi-Fi Imposters Exposed: How to Spot and Foil Evil Twin Attacks
In the vast realm of cybersecurity threats, one particularly deceptive attack technique stands out—the notorious Evil Twins. This article will…
PMKID Attacks: The Newest Threat to Your Wireless Network
What is PMKID Attack? A PMKID attack is a type of brute-force attack that can be used to crack the…
Beacon Flood Attacks: What You Need to Know
A beacon flood attack is a type of denial-of-service (DoS) attack that targets wireless networks. In a beacon flood attack,…
Authentication-Based Attack: Unveiling Wi-Fi Network Vulnerabilities
Authentication-based attacks exploit vulnerabilities in the authentication process of Wi-Fi networks to gain unauthorized access. These attacks target the weak…
Deauthentication Attack: Understanding Wi-Fi Network Disruption
Understanding the Deauthentication Attack The deauthentication attack involves the deliberate disruption of the connection between a client device and a…
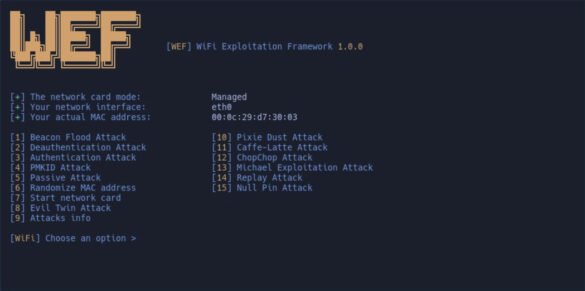
WEF | Time to get familiar with Wi-Fi Exploitation Framework
WEF is an advanced and versatile platform that encompasses a wide range of attack techniques for testing the security of…
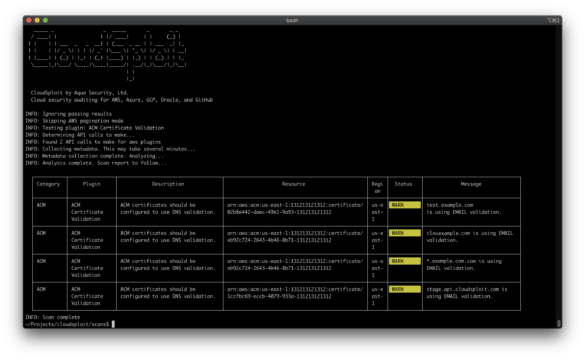
How to Protect Your Cloud Infrastructure with CloudSploit
CloudSploit is an open-source tool that helps you to identify security risks in your cloud infrastructure. It can be used…
Burp Suite: The Power of Web Application Security Testing
In today’s interconnected world, web application security is of paramount importance. Organizations need robust tools to identify vulnerabilities and protect…
Diving Deeper into the Intricacies of Burp Suite
Scanning phase involves analyzing traffic and application behavior to identify vulnerabilities and other issues. Burp Scanner uses a wide range…