SSTI: Server-Side Template Injection Guide.
What is SSTI? Server-Side Template Injection is a vulnerability where an attacker injects malicious code into a template to execute…
TorGhost | Your Best Friend in Anonymous Traffic
TorGhost is an anonymization script designed to enhance online privacy by routing all internet traffic through the Tor network. This…
7 Common Network Problems and How to Quickly Solve Them
Oh, these network problems. Despite all efforts to make everything run smoothly every day, unpleasant things happen. Below are some…
OSI Model: A Guide to Understanding Network Layers
The OSI model is a theoretical framework that helps in understanding and explaining the complexities of network communication. It breaks…
OWASP TOP 10: A2 Broken Authentication
Authentication is the process of verifying a user’s identity. Broken authentication is a vulnerability that allows attackers to gain unauthorized…
Port Scanning Methods with Nmap
Nmap is a security auditing tool used in the field of cybersecurity for actively enumerating a target system/network. It is…
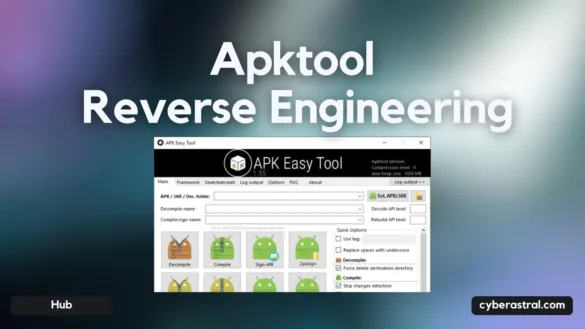
Apktool | Reverse Engineering Tool
It is a tool for reverse engineering 3rd party, closed, binary Android apps. It can decode resources to nearly original…
What is DNS Spoofing?
Today, the internet has become an integral part of our lives. From banking to shopping to travel, every aspect of…
Repository With Free Anonymous Proxies
proxy-list GitHub repository containing anonymous HTTP, SOCKS4, SOCKS5 proxies that are updated and checked approximately every 15 minutes. The repository…
Hackers Exploit Zero-Day Vulnerability to Compromise Cisco Devices
More than 40,000 Cisco devices running the IOS XE operating system have fallen victim to an exploit following the discovery…