Today, the internet has become an integral part of our lives. From banking to shopping to travel, every aspect of our lives is connected to the internet.
As the internet is widely used these days, cybersecurity is a major concern for most web users, given the increasing news about new cyberattacks.
Currently, the concept of a cyber attack is very common, and it has become a growing headache for many IT companies and enterprises. In recent years, some major names, such as Google, The New York Times, and others, have fallen victim to cyberattacks. In today’s post, we will learn about DNS attacks, how they work, and how to combat them.
What is DNS Spoofing?
Indeed, DNS attacks occur when a hacker is able to find vulnerabilities for subsequent exploitation in the Domain Name System (DNS).
Hackers exploit vulnerabilities, making DNS attacks possible. To understand how DNS attacks work, you first need to understand how DNS works.
For those who don’t know, the Domain Name System (DNS) is a protocol that interprets alphanumeric (letter-based) domain names into IP addresses. In short, its primary function is to translate user-friendly domain names into IP addresses, which are more convenient for computers.
How Does DNS Work?
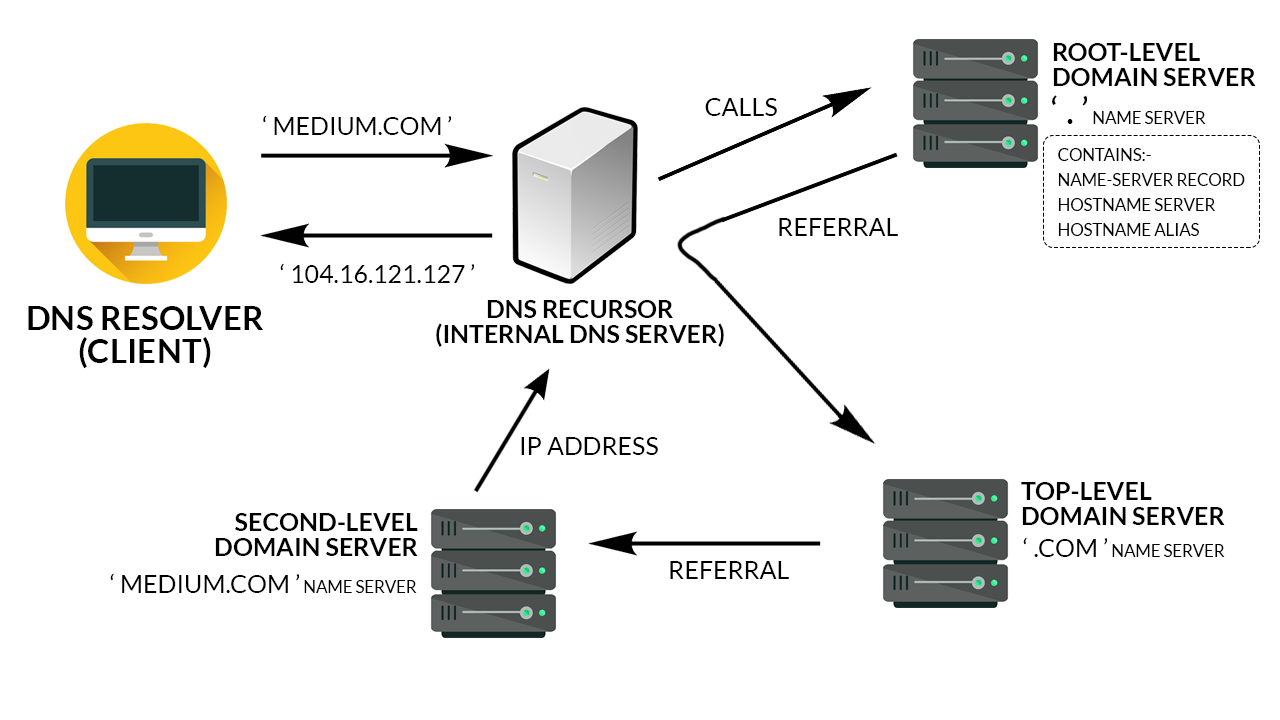
When a user enters a domain name into their browser, the program, available in the operating system known as a “DNS resolver,” looks for the IP address of that domain name.
First, the DNS resolver looks in its own local cache to check if it already has the IP address for that domain. If it doesn’t find it in the local cache, it requests the DNS server to check if it knows the exact IP address for that domain.
DNS servers work in a recursive manner, meaning they can ask each other to find the DNS server that knows the correct IP address for the domain name.
Once the DNS resolver finds the IP address, it returns it to the requesting program. DNS caches the domain address for future use.
While the Domain Name System is powerful, it may seem less oriented toward security. This is possibly why we see various types of DNS attacks.
To minimize the potential for DNS attacks, server administrators should take some necessary steps. They can use updated DNS software and regularly configure servers for redundancy. On a personal level, users can clear their DNS cache to avoid security threats. If you don’t know how to clear your DNS cache, you can read a relevant informative post on hostinger.com.
How Hackers Exploit DNS?
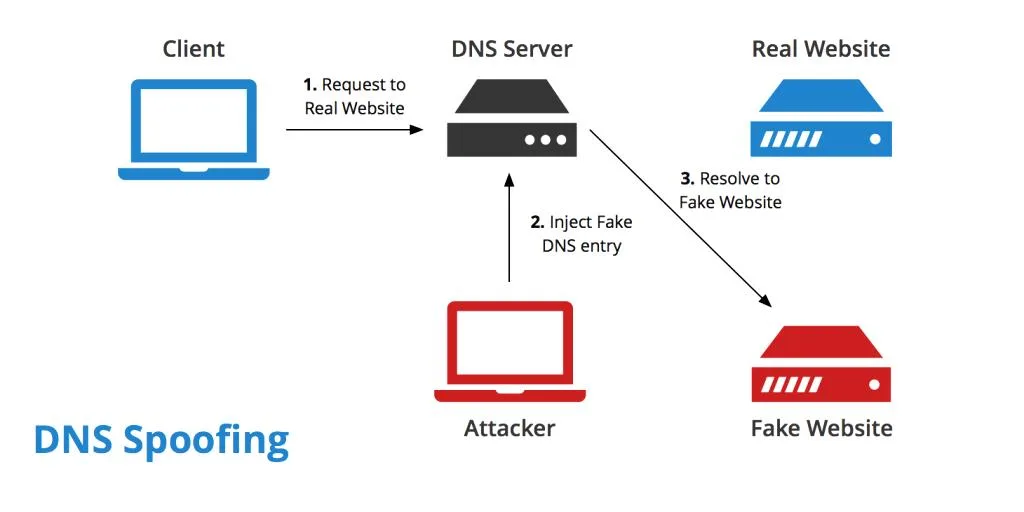
The biggest problem with the DNS system is that if an attacker can find a way to replace an authorized IP address of a website with a stolen one, anyone trying to access that website will be redirected to a fraudulent address. The user won’t have the slightest idea that they’re going to the wrong address.
One of the main issues with DNS server configuration is that it doesn’t remember its default settings. Attackers take advantage of this loophole.
Main Types of DNS Attacks
In recent years, there has been a sharp increase in DNS attacks. And these attacks are not limited to small websites.
Many popular sites, such as Reddit, Spotify, Twitter, have also reported their unavailability to thousands of their users.
As DNS attacks become more common, we need to learn to identify DNS attacks so that we can better deal with the situation. Let’s look at the types of DNS attacks.
Zero-Day Attack: In this type of attack, an attacker exploits a previously unknown vulnerability in DNS server software or protocol stack.Fast Flux DNS: Hackers change the DNS record frequency to redirect DNS queries. This method helps the attacker avoid detection.DNS Spoofing: Also known as DNS cache poisoning, this is a type of computer security breach. Attackers or hackers corrupt the entire DNS server by replacing an authorized IP address with a fake IP address in the server’s cache. This way, they redirect all traffic to a malicious website and collect sensitive information.Man in the Middle (MITM): This method involves intercepting communications between users and a DNS server to redirect them to a different or malicious IP address. By positioning themselves between the user and the DNS server, attackers can manipulate the DNS responses and lead users to unintended destinations.DNS Server Compromise: In this method, attackers hijack a DNS server configured to return a malicious IP address. By compromising the DNS server, they gain control over the DNS resolution process and can manipulate the responses to redirect users to malicious sites.Exploiting Time-To-Live (TTL): This method exploits the DNS server cache’s Time-To-Live (TTL) values. Attackers manipulate the TTL values to ensure incorrect DNS entries persist for more extended periods. By doing so, they increase the number of potential victims and prolong the duration of the attack. Even users who were not initially targeted can be redirected to malicious sites if the corrupt DNS responses remain in the cache.
Each method poses a significant threat to the integrity and security of DNS resolution, highlighting the importance of implementing robust defenses against DNS spoofing attacks.
This is one of the most popular phishing techniques that malicious actors regularly use for data theft. Since users type the correct domain address into their browsers, they never realize they are accessing a fake or stolen website.
Therefore, it becomes harder to detect this attack. Sometimes, users cannot identify it until the time to live (TTL) expires. TTL, or time to live, is the time that a DNS resolver remembers a DNS query before it expires.
The best way to minimize DNS cache poisoning attacks is to periodically clear your DNS cache.
DDoS Attack on DNS
A DDoS attack, or Distributed Denial-of-Service attack, occurs when multiple systems flood the resources of the target system. Attackers can use this attack against various types of systems, including DNS servers.
A DDoS attack can lead to the failure of the entire DNS server, making the internet inaccessible to users. However, they can still access websites they’ve recently visited if they are stored in the local cache.
An attack on a DNS server can be a significant network security problem. Therefore, it should not be taken lightly by businesses. They should implement the most advanced security measures to reduce risks and prevent the consequences of such attacks.
How to Protect Against This Attack
Depends on the Role of Your Systems in the Environment. However, you can take the following steps.
Gain regular insight into what’s happening in the network. You can use technologies such as IPFIX, NetFlow, etc., to achieve the desired results.
DDoS attacks usually gain network access with an excessive packet transmission rate. Therefore, you should think about various ways to address such issues.