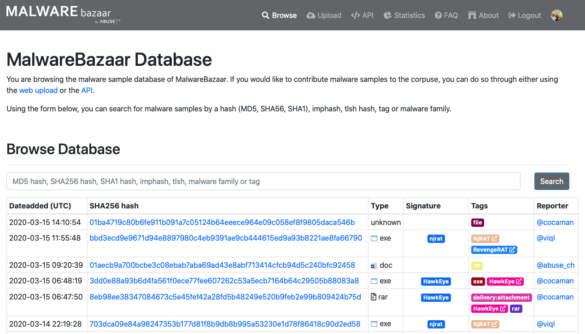
MalwareBazaar – Malware Sample Database
MalwareBazaar is a comprehensive platform that provides an extensive collection of malware samples, offering a unique opportunity for researchers, cybersecurity…
Secure Your Website with Security Headers (Windows/Linux)
With the rise of cybersecurity threats, protecting your website and its visitors is of utmost importance. One effective way to…
Defending Against Zero-Click Attacks: The Silent Threat
Zero-click attacks have emerged as a formidable challenge for organizations, as they exploit vulnerabilities without any user interaction,…
Hacking a Company with 0-Click Email Attack
Phishing Attacks Phishing attacks have emerged as a prominent method employed by malicious actors. Among the various tactics used, a…
Defending Against Cafe-Latte: Strengthening Wi-Fi Security
Understanding the Cafe-Latte Attack The Cafe-Latte Attack targets the weaknesses in the WEP encryption protocol, which was widely used in…
Securing Wi-Fi: Mitigating the Michael Attack Threat
Understanding the Michael Attack The Michael Attack is a cryptographic exploit that targets the TKIP encryption protocol, primarily used in…
Replay Attack: Deceptive Echoes in Cybersecurity
In the vast landscape of cybersecurity, a cunning technique known as the Replay Attack echoes as a haunting threat. This…
ChopChop Attack: Wi-Fi Encryption Unraveled
In the realm of wireless network security, a cunning technique known as the ChopChop attack has emerged, capable of dismantling…
Null PIN Attack: Breaching Wi-Fi Defenses Without a Trace
In the realm of Wi-Fi security, the Null PIN Attack has emerged as a potent method for bypassing the safeguards…
Cracking the WPS Code: Understanding and Preventing the Pixie Dust Attack
In the realm of Wi-Fi security, an intriguing vulnerability known as the Pixie Dust Attack has captured the attention of…